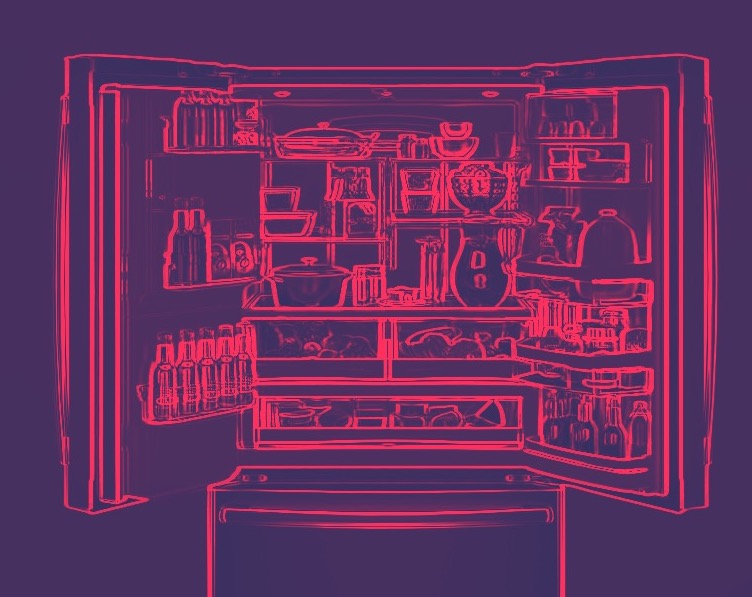
Appliance-based malwareCase studyMany people are susceptible to cyber attacks nowadays
and it doesn’t only happen through computer networks. The built-in
electronics inside home appliances are a possible entry for malware!
|
 |
|---|
How does it work? Often, these kinds of attacks that infect
appliances with botnet malware, do not impact the person
owning those appliances, but bigger businesses.
Thus, the homeowner stays secure and safe and might
not even notice anything wrong.
|
 |
|---|
How to protect ourselves from appliance-based malware?
Only device manufacturers can protect us from these attacks.
So how do manufacturers fight this type of attack? How can they ensure that home appliances do not get infected
with malware and cause disorder?
Security is implemented in the design process for the appliance
itself, its various electronic components and control surfaces.
Most home appliance manufacturers obtain their control units from
a wide network of smaller manufacturers, sometimes with a global
supply chain. These vendors must ensure that the chips and the
components they use are tamper-proof.
security practices that should be used by appliance makers:
ConclusionMost consumer product and device manufacturers are well-informed about the potential for attacks on smart devices such as door locks, baby monitors, and home thermostats, but this risk awareness must extend to types of connected systems, including home appliances. These systems have been attacked and used to distribute malware. Keeping these devices secure is essential to protect your home network, slow the spread of malware, and even protect credit card numbers or other personal data stored on smart home devices. |
 |
|---|
Appliance Based Malware |
Arina Shteyn |
|
|---|